iOS jailbreaking is back! What you need to know about the new exploits.
Jailbreaking. It is a term that has garnered a lot of cultural allure, something about it conjures the image of an elite hacker sitting in a dark basement trying to jailbreak a mainframe or whatever those cool hollywood hackers do these days, but really jailbreaking is a lot less exciting than that. Jailbreaking is simply gaining root access (access that is at the highest privilege level) to a system that is designed to keep you sandboxed (basically isolated) in a special user space at a lower privilege level. Jailbreaking allows you to load custom programs, new games, modify the way the operating system works to improve usability and more. It goes by different names on different systems. but they all mean the same thing. On video game consoles it is most commonly referred to as “homebrewing,” on Android it is rather creatively named “rooting,” and on iOS it goes by the name “jailbreaking.” With the exception of modern Android phones, this process relies on a security exploit allowing a piece of code to escape the user space without permission and modify the operating system to allow unsigned code to run as root. This of course means that it has become less common with time as companies get better at writing secure code.
Of the current generation of consoles only a few early production model Nintendo Switches can be fully homebrewed. This is because of an unpatchable “bootloader” (the bootloader is code that is in charge of booting the system/loading the OS) exploit that allow the user to execute unsigned code before the OS loads. The Xbox One has an official way to run unsigned games (but it is still only in user space), and the PS4 can only be homebrewed on a two year old firmware version. For a long time, it seemed like the iOS jailbreaking scene was dying as well. Apple had simply become too good at patching exploits for a stable jailbreak to exist, only Android rooting had remained relatively strong, as some Android phones had a switch to allow the user to choose to allow the bootloader to run unsigned code if it is uploaded to the device. While this is similar in theory to the Switch’s bootloader exploit, it exists by design instead of by mistake. With all this talk about the bootloader being the way most modern jailbreaks work in an article on iOS jailbreaking you might not be surprised to hear that iOS
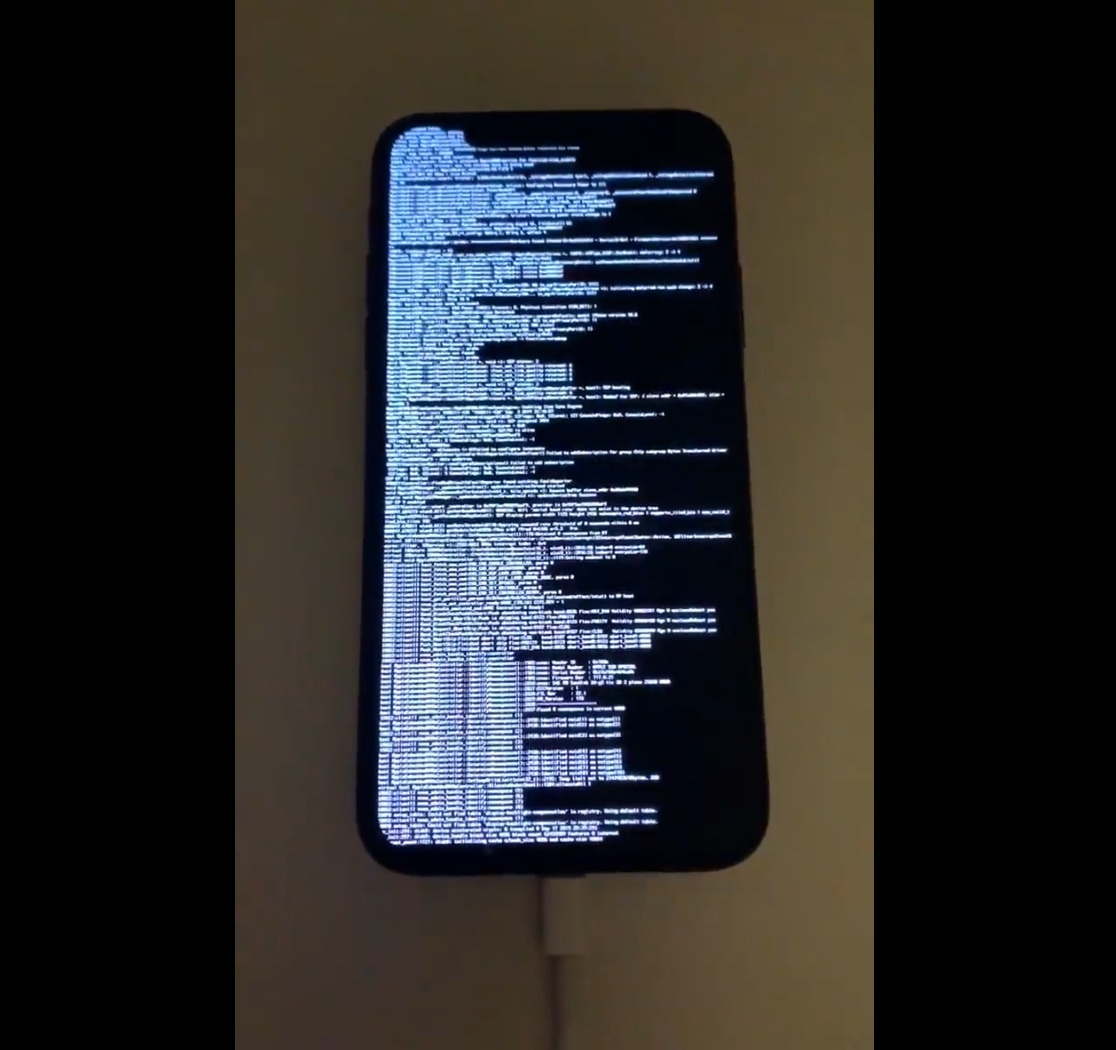
devices had their own bootloader (or as it is often called “boot rom”) exploit. Like the exploit on the Switch the “checkm8” (pronounced checkmate) exploit on iOS is unpatchable in software, due to it running before the OS loads. This
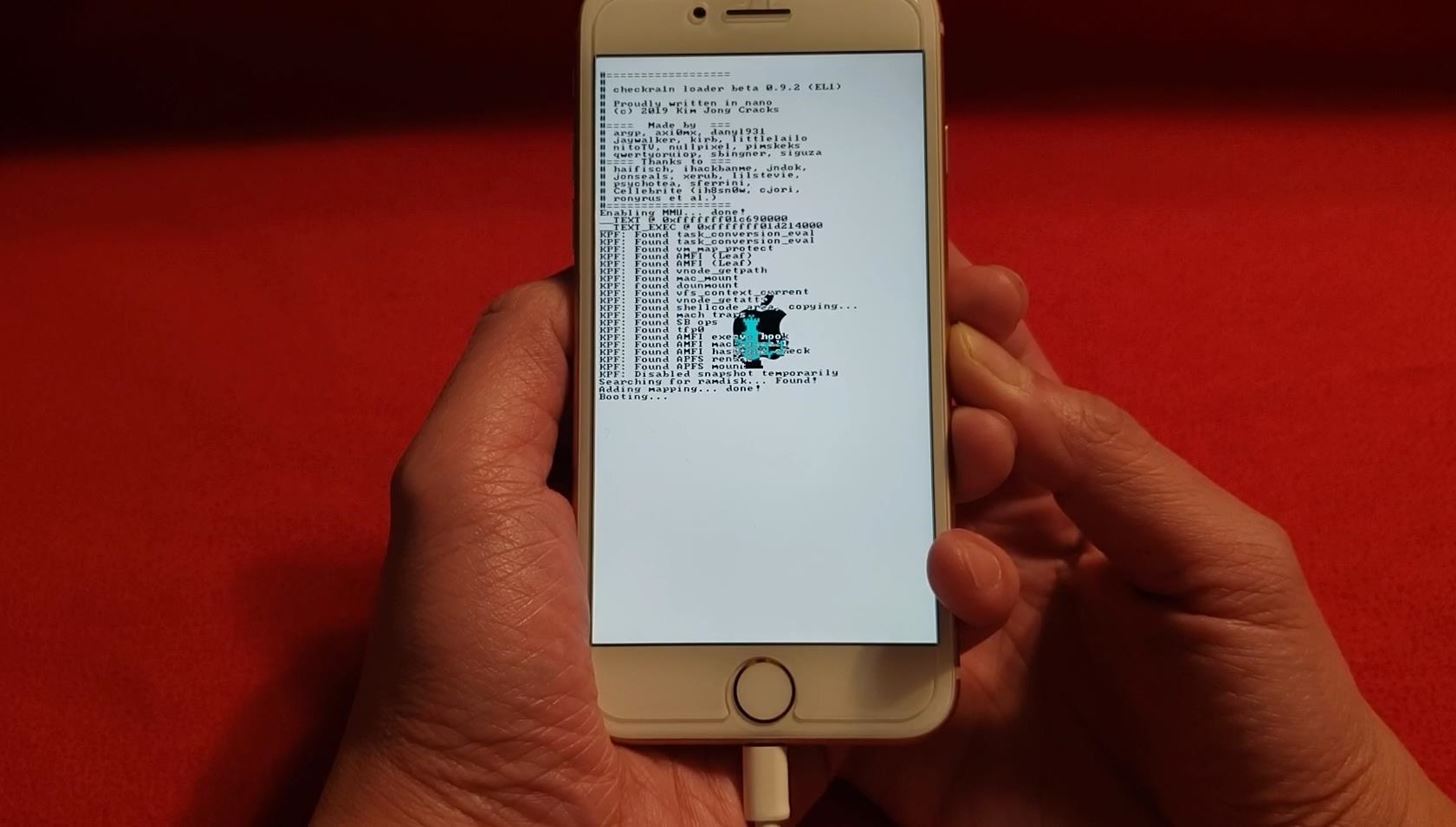
means it can work on any iOS version, and it affects all iOS devices up to the iPhone X, after which Apple was able to update the hardware to change how the boot rom works. The checkm8 exploit uses an overflow bug to overwrite Apple’s boot code and inject their own code. The program “checkra1n” (pronounced checkrain) allows you to run this exploit to get a functional jailbreak on your own device. It is available for Linux and Mac OS at https://checkra.in/
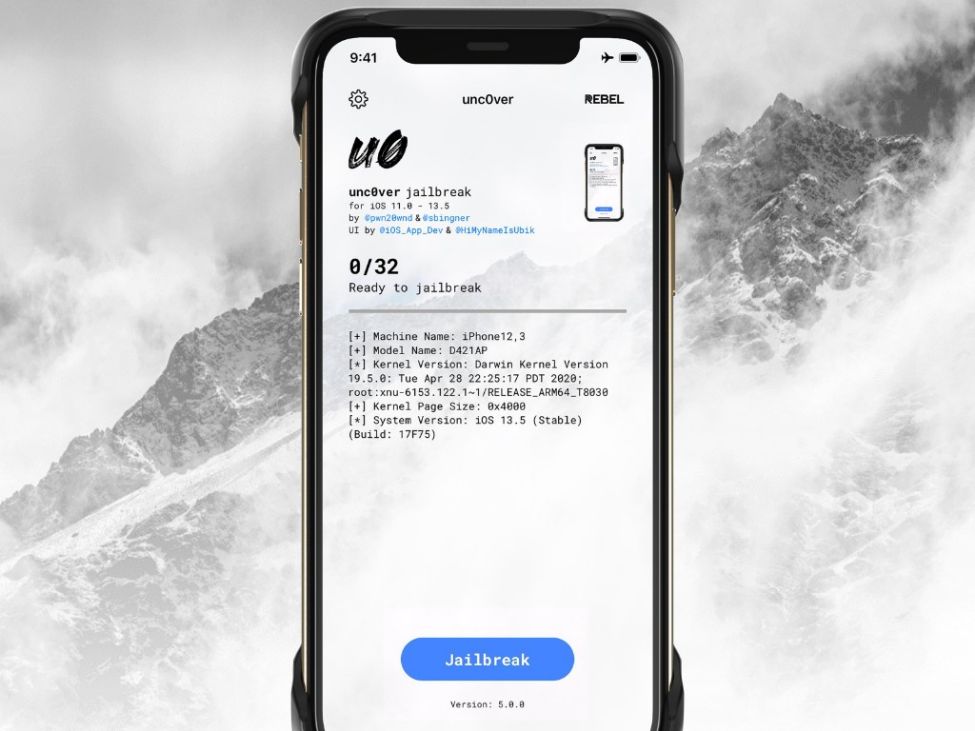
But what if you have a newer phone with a patched boot rom? Well, fear not my friend, for there is an exploit for you as well! “unc0ver” (pronounced uncover… are you figuring out how l33t speak works yet…?) is a good old fashioned jailbreak. It runs in the OS itself, which means that it can be patched out, but it currently works on all iOS versions up to iOS 13.5 (which at the time of writing is the latest version.) It can be downloaded from https://unc0ver.dev/ and requires you to sideload an app to your phone, which can be done on Windows or Mac OS by using the Altstore program.
All of these exploits promise an exciting future for the world of iOS hacking, however if you don’t intend to jailbreak, it might not hurt to upgrade your iOS version as soon as a patch is available, as you don’t want a malicious hacker to be able to gain root privileges into your phone through the same exploit used by unc0ver.
